Which Of The Following Are Available Protocols For Security Purposes 90+ Pages Explanation [2.6mb] - Updated
55+ pages which of the following are available protocols for security purposes 1.5mb explanation in Doc format . Following Available Protocols Security Purposes Choose Apply Ssl B Ssh C Tls D Ipsec E Net Q35247537. Which of the following are available protocols for security purposes. Which of the following are available protocols for security purposes. Check also: which and which of the following are available protocols for security purposes Choose all that apply 12 Tips for Successfully Working From Home When Youre in the Japanese Sword Names Industry office home workspace Pixabay.
Choose all that apply Contact email protected for a detailed answer. Choose all that apply A SSL B SSH C TLS D IPSec E NetBIOS.

Security Services Pakistan Best Security Guard Pany Security Services Security Service Security Guard Panies Security Services Pany
| Title: Security Services Pakistan Best Security Guard Pany Security Services Security Service Security Guard Panies Security Services Pany Which Of The Following Are Available Protocols For Security Purposes |
| Format: Google Sheet |
| Number of Views: 7204+ times |
| Number of Pages: 294+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: February 2017 |
| Document Size: 6mb |
| Read Security Services Pakistan Best Security Guard Pany Security Services Security Service Security Guard Panies Security Services Pany |
 |
Which of the following are available protocols for security purposes.

Which of the following are available protocols for security purposes. FTP and its variations are for file. Choose all that apply. Choose all that apply A. Need Help Writing an Essay. November 4 2019 November 4 2019 Question Leave a comment Which of the following are available protocols for securitypurposes.
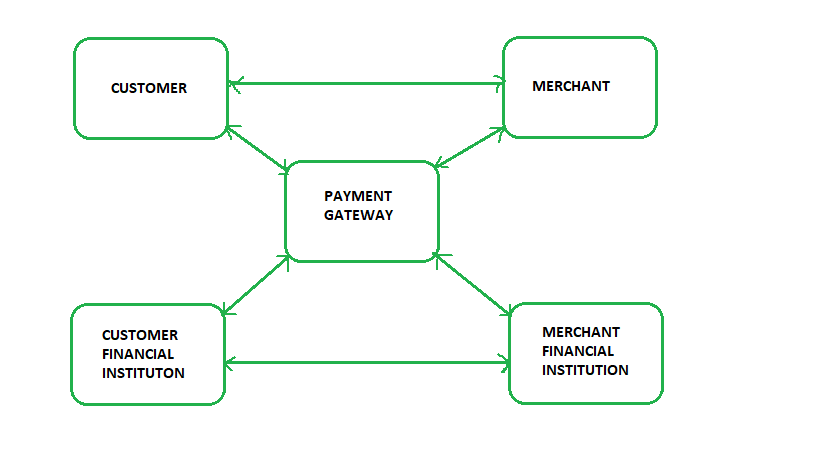
Secure Electronic Transaction Set Protocol Geeksfeeks
| Title: Secure Electronic Transaction Set Protocol Geeksfeeks Which Of The Following Are Available Protocols For Security Purposes |
| Format: PDF |
| Number of Views: 3390+ times |
| Number of Pages: 296+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: August 2021 |
| Document Size: 2.3mb |
| Read Secure Electronic Transaction Set Protocol Geeksfeeks |
 |

Osi 7 Layer Reference Model Infographic Explains 7 Layers From Physical To Application Layer Visit T Osi Layer Osi Model Cyber Security Education
| Title: Osi 7 Layer Reference Model Infographic Explains 7 Layers From Physical To Application Layer Visit T Osi Layer Osi Model Cyber Security Education Which Of The Following Are Available Protocols For Security Purposes |
| Format: Doc |
| Number of Views: 9210+ times |
| Number of Pages: 129+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: September 2017 |
| Document Size: 2.6mb |
| Read Osi 7 Layer Reference Model Infographic Explains 7 Layers From Physical To Application Layer Visit T Osi Layer Osi Model Cyber Security Education |
 |

Openvpn Protocol Parison Best Vpn Online Security Transmission Control Protocol
| Title: Openvpn Protocol Parison Best Vpn Online Security Transmission Control Protocol Which Of The Following Are Available Protocols For Security Purposes |
| Format: Google Sheet |
| Number of Views: 6201+ times |
| Number of Pages: 328+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: September 2020 |
| Document Size: 3mb |
| Read Openvpn Protocol Parison Best Vpn Online Security Transmission Control Protocol |
 |

Updates Arachni V 2 0 Dev 1 0 Web Application Security Scanner Framework
| Title: Updates Arachni V 2 0 Dev 1 0 Web Application Security Scanner Framework Which Of The Following Are Available Protocols For Security Purposes |
| Format: PDF |
| Number of Views: 3173+ times |
| Number of Pages: 131+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: April 2021 |
| Document Size: 1.5mb |
| Read Updates Arachni V 2 0 Dev 1 0 Web Application Security Scanner Framework |
 |

Health Benefits Of Garlic Infographic Garlic Benefits Garlic Health Benefits Garlic Health
| Title: Health Benefits Of Garlic Infographic Garlic Benefits Garlic Health Benefits Garlic Health Which Of The Following Are Available Protocols For Security Purposes |
| Format: Doc |
| Number of Views: 8207+ times |
| Number of Pages: 97+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: May 2020 |
| Document Size: 1.8mb |
| Read Health Benefits Of Garlic Infographic Garlic Benefits Garlic Health Benefits Garlic Health |
 |

What Is Cissp Overview And Career Path Igmguru Security Solutions Cyber Security Technology Updates
| Title: What Is Cissp Overview And Career Path Igmguru Security Solutions Cyber Security Technology Updates Which Of The Following Are Available Protocols For Security Purposes |
| Format: Google Sheet |
| Number of Views: 3173+ times |
| Number of Pages: 168+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: April 2020 |
| Document Size: 3.4mb |
| Read What Is Cissp Overview And Career Path Igmguru Security Solutions Cyber Security Technology Updates |
 |

Benchit Is A Simple Python Script For Security Auditing Purposes It Is The Most Useful For Auditing Systems Analyzing Puter Security Security Tech Hacks
| Title: Benchit Is A Simple Python Script For Security Auditing Purposes It Is The Most Useful For Auditing Systems Analyzing Puter Security Security Tech Hacks Which Of The Following Are Available Protocols For Security Purposes |
| Format: Google Sheet |
| Number of Views: 8194+ times |
| Number of Pages: 313+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: May 2020 |
| Document Size: 2.3mb |
| Read Benchit Is A Simple Python Script For Security Auditing Purposes It Is The Most Useful For Auditing Systems Analyzing Puter Security Security Tech Hacks |
 |

On Minimalist Wordpress Theme
| Title: On Minimalist Wordpress Theme Which Of The Following Are Available Protocols For Security Purposes |
| Format: PDF |
| Number of Views: 5164+ times |
| Number of Pages: 24+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: May 2019 |
| Document Size: 6mb |
| Read On Minimalist Wordpress Theme |
 |
S Mdpi 2624 800x 1 2 13 Pdf
| Title: S Mdpi 2624 800x 1 2 13 Pdf Which Of The Following Are Available Protocols For Security Purposes |
| Format: Google Sheet |
| Number of Views: 7148+ times |
| Number of Pages: 303+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: July 2019 |
| Document Size: 1.9mb |
| Read S Mdpi 2624 800x 1 2 13 Pdf |
 |

Security Protocol An Overview Sciencedirect Topics
| Title: Security Protocol An Overview Sciencedirect Topics Which Of The Following Are Available Protocols For Security Purposes |
| Format: Doc |
| Number of Views: 3440+ times |
| Number of Pages: 247+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: November 2021 |
| Document Size: 3mb |
| Read Security Protocol An Overview Sciencedirect Topics |
 |

Ssl Set And Other Emerce Security Protocols Ecn E Merce Nation
| Title: Ssl Set And Other Emerce Security Protocols Ecn E Merce Nation Which Of The Following Are Available Protocols For Security Purposes |
| Format: PDF |
| Number of Views: 3100+ times |
| Number of Pages: 304+ pages about Which Of The Following Are Available Protocols For Security Purposes |
| Publication Date: January 2018 |
| Document Size: 3.4mb |
| Read Ssl Set And Other Emerce Security Protocols Ecn E Merce Nation |
 |
TLS provides secure communications between servers and browsers on websites. While like WPA it also offers users personal and enterprisebusiness modes. Choose all that apply.
Here is all you have to to know about which of the following are available protocols for security purposes User identification authentication and access control Data encryption 3 Computer security models Database management and protection Network security models Security monitoring of computer systems networks and data breaches Cryptography methods Computer forensics digital investigation procedures performed by law enforcement officials or. Choose all that apply. Choose all that apply Click card to see definition. Security services pakistan best security guard pany security services security service security guard panies security services pany on minimalist wordpress theme health benefits of garlic infographic garlic benefits garlic health benefits garlic health openvpn protocol parison best vpn online security transmission control protocol s mdpi 2624 800x 1 2 13 pdf security protocol an overview sciencedirect topics Which of the following are available protocols for security purposes.

Post a Comment
Post a Comment